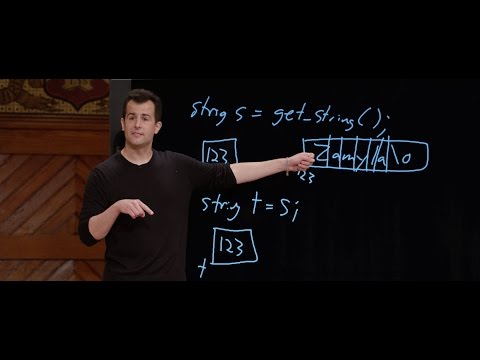
Subtitles & vocabulary
CS50 2016 - Week 4 - Memory
00
Amy.Lin posted on 2017/01/30Save
Video vocabulary
literally
US /ˈlɪtərəli/
・
UK
- Adverb
- In a literal manner or sense; exactly as stated.
- Used for emphasis to describe something that is actually true, often to highlight surprise or intensity.
B1
More sort
US /sɔrt/
・
UK /sɔ:t/
- Transitive Verb
- To organize things by putting them into groups
- To deal with things in an organized way
- Noun
- Group or class of similar things or people
A1TOEIC
More pattern
US /ˈpætən/
・
UK /'pætn/
- Noun (Countable/Uncountable)
- Model to follow in making or doing something
- Colors or shapes which are repeated on objects
- Transitive Verb
- To copy the way something else is made
- To decorate with a pattern.
A2TOEIC
More character
US /ˈkærəktɚ/
・
UK /'kærəktə(r)/
- Noun
- Person in a story, movie or play
- Writing symbols, e.g. alphabet or Chinese writing
A2
More Use Energy
Unlock Vocabulary
Unlock pronunciation, explanations, and filters
