Subtitles & vocabulary
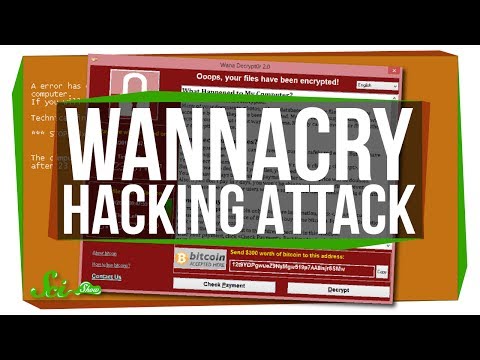
Why Was the WannaCry Attack Such a Big Deal?
00
mommy posted on 2017/11/07Save
Video vocabulary
vulnerable
US /ˈvʌlnərəbəl/
・
UK /ˈvʌlnərəbl/
- Adjective
- Being open to attack or damage
- Being easily harmed, hurt, or wounded
B1
More episode
US /ˈɛpɪˌsod/
・
UK /'epɪsəʊd/
- Noun
- One separate event in a series of events
- Show which is part of a larger story
B1TOEIC
More massive
US /ˈmæsɪv/
・
UK /ˈmæsɪv/
- Adjective
- Very big; large; too big
- Large or imposing in scale or scope.
B1
More sophisticated
US /səˈfɪstɪˌketɪd/
・
UK /səˈfɪstɪkeɪtɪd/
- Adjective
- Making a good sounding but misleading argument
- Wise in the way of the world; having refined taste
- Transitive Verb
- To make someone more worldly and experienced
B1TOEIC
More Use Energy
Unlock Vocabulary
Unlock pronunciation, explanations, and filters
